OpenStack Services
OpenStack Services
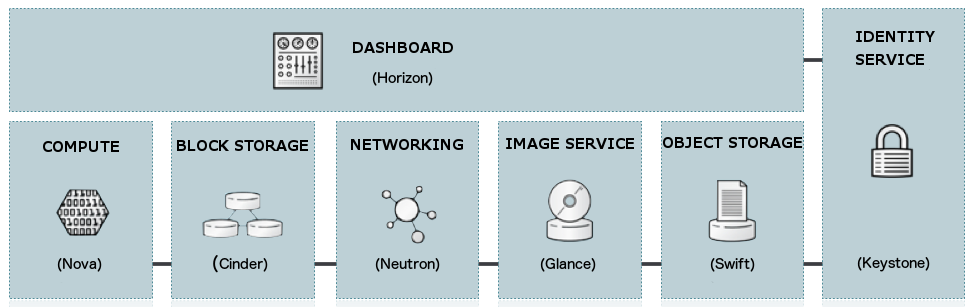
Compute¶
OpenStack Compute service (nova) provides services to support the management of virtual machine instances at scale, instances that host multi-tiered applications, dev/test environments, “Big Data” crunching Hadoop clusters, and/or high performance computing.
The Compute service facilitates this management through an abstraction layer that interfaces with supported hypervisors, which we address later on in more detail.
Later in the guide, we focus generically on the virtualization stack as it relates to hypervisors.
For information about the current state of feature support, see OpenStack Hypervisor Support Matrix.
The security of Compute is critical for an OpenStack deployment. Hardening techniques should include support for strong instance isolation, secure communication between Compute sub-components, and resiliency of public-facing API endpoints.
Object Storage¶
The OpenStack Object Storage service (swift) provides support for storing and retrieving arbitrary data in the cloud. The Object Storage service provides both a native API and an Amazon Web Services S3 compatible API. The service provides a high degree of resiliency through data replication and can handle petabytes of data.
It is important to understand that object storage differs from traditional file system storage. It is best used for static data such as media files (MP3s, images, videos), virtual machine images, and backup files.
Object security should focus on access control and encryption of data in transit and at rest. Other concerns may relate to system abuse, illegal or malicious content storage, and cross authentication attack vectors.
Block Storage¶
The OpenStack Block Storage service (cinder) provides persistent block storage for compute instances. The Block Storage service is responsible for managing the life-cycle of block devices, from the creation and attachment of volumes to instances, to their release.
Security considerations for block storage are similar to that of object storage.
Networking¶
The OpenStack Networking service (neutron, previously called quantum) provides various networking services to cloud users (tenants) such as IP address management, DNS, DHCP, load balancing, and security groups (network access rules, like firewall policies). It provides a framework for software defined networking (SDN) that allows for pluggable integration with various networking solutions.
OpenStack Networking allows cloud tenants to manage their guest network configurations. Security concerns with the networking service include network traffic isolation, availability, integrity and confidentiality.
Dashboard¶
The OpenStack Dashboard (horizon) provides a web-based interface for both cloud administrators and cloud tenants. Through this interface administrators and tenants can provision, manage, and monitor cloud resources. Horizon is commonly deployed in a public facing manner with all the usual security concerns of public web portals.
Identity service¶
The OpenStack Identity service (keystone) is a shared service that provides authentication and authorization services throughout the entire cloud infrastructure. The Identity service has pluggable support for multiple forms of authentication.
Security concerns here pertain to trust in authentication, management of authorization tokens, and secure communication.
Image service¶
The OpenStack Image service (glance) provides disk image management services. The Image service provides image discovery, registration, and delivery services to the Compute service, as needed.
Trusted processes for managing the life cycle of disk images are required, as are all the previously mentioned issues with respect to data security.
Data processing service¶
The Data Processing service for OpenStack (sahara) provides a platform for the provisioning, management, and usage of clusters running popular processing frameworks.
Security considerations for data processing should focus on data privacy and secure communications to provisioned clusters.
Other supporting technology¶
OpenStack relies on messaging for internal communication between several of its services. By default, OpenStack uses message queues based on the AMQP. Similar to most OpenStack services, it supports pluggable components. Today the implementation back end could be RabbitMQ, Qpid, or ZeroMQ.
As most management commands flow through the message queuing system, it is a primary security concern for any OpenStack deployment. Message queuing security is discussed in detail later in this guide.
Several of the components use databases though it is not explicitly called out. Securing the access to the databases and their contents is yet another security concern, and consequently discussed in more detail later in this guide.
Source: http://docs.openstack.org/security-guide/introduction/introduction-to-openstack.html